On June 1st, 2018, I officially became a Certified Information Systems Security Professional (CISSP). This post will very closely mirror a previous post, Becoming a CEH, as I used many of the same resources. I’m transitioning out of the military and I want to work in cyber security. Several months ago, I set in motion my plan to get two or three certifications that covered as much of the DoD Approved 8570 Baseline Certifications table as possible. I decided on pursuing the CEH and the CISSP initially, which together would cover 12 of 14 categories/levels. Since I am writing this from the perspective of a transitioning service member, some of the resources I mention will be limited to and/or geared toward active service members and/or veterans.
Becoming a CEH
On March 26th, 2018, I became a Certified Ethical Hacker. You see, I’m transitioning out of the military soon and I want to work in cyber security. A few months ago, I set in motion my plan to get two or three certifications that covered as much of the DoD Approved 8570 Baseline Certifications table as possible. I decided on pursuing the CEH and the CISSP (more on that in a later post updated post; I passed!), which together would cover 12 of 14 categories/levels. Since I am writing this from the perspective of a transitioning service member, some of the resources I mention will be limited to and/or geared toward active service members and/or veterans. Also keep in mind that 12 days before I sat for my exam, EC-Council announced v10 of the CEH, as well as the CEH Practical. I would venture to guess v10 has much of the same material and that you would be ok using only these resources, but keep an eye out for updated versions of the resources I mention. Read More
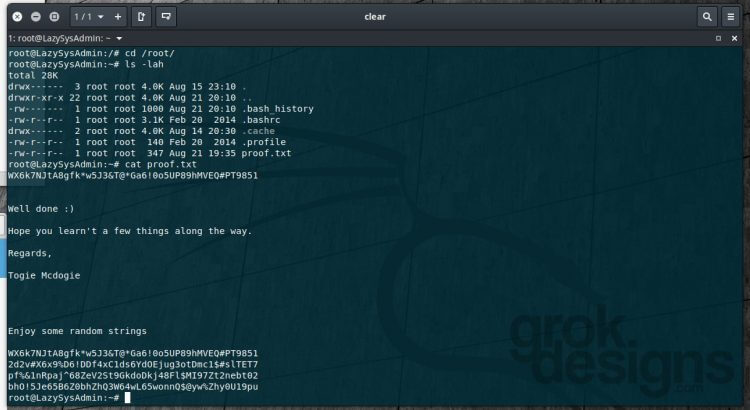
VulnHub Walk-through – LazySysAdmin: 1
This is the first walk-through I have written for a VulnHub machine. Please send any feedback if you have ideas for improving it!
Today we’ll see if we can obtain root access to the LazySysAdmin: 1 machine from VulnHub.

Home Lab v4.0…ish
When do you upgrade your home lab version? New hardware? New arrangement? I’m not really sure, so we’re going to go with v4.0.
This post is really just an overview of what the lab currently looks like and some of the functions it performs. A lot of it is more production than lab, so…labduction?
There she is, up there, in all of her cobbled together glory. And trust me, I’m cleaning up the cabling this weekend! I wish I’d known when I started what I know now, but I suppose that’s part of the reason we do this! Read More
pfSense IKEv2 for iOS/macOS – Part 4
In this article, we’ll configure On Demand VPN for iOS and macOS devices to connect to the VPN we created.
Articles in This Series:
Part 1 – Certificate Configuration
Part 2 – VPN Configuration
Part 3 – Mobile Profile Configuration
Part 4 (Current Article)
Part 4 – On Demand VPN
So you want to get your hands dirty and force your VPN to connect based on network states? You’ve come to the right place! First and foremost, you’ll need an editor that handles XML. I recommend Atom.
Inspired by a Reddit post1, I began to look into Apple’s options for forcing VPN connections through the use of Mobile Configuration Profiles2. One resource I found that was helpful was this post from derman.com. So open up your Mobile Configuration file and let’s get to work! Read More
pfSense IKEv2 for iOS/macOS – Part 3
In this article, we’ll configure an Apple Mobile Configuration Profile for iOS and macOS devices to connect to the VPN we created.
Articles in This Series:
Part 1 – Certificate Configuration
Part 2 – VPN Configuration
Part 3 (Current Article)
Part 4 – On Demand VPN Read More
pfSense IKEv2 for iOS/macOS – Part 2
In this article, we’ll configure an IKEv2 VPN in pfSense for our iOS and macOS devices to connect to.
Articles in This Series:
Part 1 – Certificate Configuration
Part 2 (Current Article)
Part 3 – Mobile Profile Configuration
Part 4 – On Demand VPN
At this point, we’ve configured our server certificates. Now let’s create the actual VPN. Read More
pfSense IKEv2 for iOS/macOS – Part 1
In this article, we’ll configure the certificates necessary to set up an IKEv2 VPN in pfSense.
Articles in This Series:
Part 1 (Current Article)
Part 2 – VPN Configuration
Part 3 – Mobile Profile Configuration
Part 4 – On Demand VPN
This was setup and configured with the following: macOS 10.13 High Sierra Beta (should work with 10.12+, possibly older), and Apple Configurator 2.5 Beta (available from the Apple Developer site/release available on the App Store; should work with prior versions).
This tutorial has its foundation in a thread1 on the pfSense Forums, however I have made some changes that will be outlined here. Let’s get started! Read More
pfSense Router Upgrade
I recently replaced my home pfSense router, previously a Zotac CI323, with a Qotom Q355G4. While the Zotac was never a bad machine as a router, it wasn’t great, and as my needs began to expand, so too did my issues. I frequently experienced a complete failure of the WAN link, only solved by rebooting, and when running Suricata, a saturated WAN link meant a quick performance degradation to the point where I completely lost internet access and could not access the pfSense web interface or SSH. Read More